A few years ago, your author took possession of what was then the latest version of SuSE Linux. For the first time, this version allowed you to easily encrypt a whole filesystem right from the start (it was always possible to do before then, but required a lot of obscure command line magic).
Interested in trying this out, I encrypted my /home filesystem – meaning that at boot time I had to enter a lengthy passphrase to decrypt it and then, whilst running, the filesystem would act normally.
Unfortunately, I stopped using that particular computer for a few weeks and when I came back I couldn’t for the life of me remember the passphrase. I spent hours trying everything I could think of. I hunted through notebooks to see if I’d written it down. All to no avail.
In a stroke of what I can only describe as pure genius, I had installed a utility to remember all my passwords and passphrases with just one master passphrase (which I could remember just fine). Where had I installed that utility? In my /home filesystem, of course.
This episode proved two things to me (three if you include the revelation that I can be really dumb sometimes). First was that I was using some pretty serious encryption to protect things that didn’t really warrant protection: it turned out that even I wasn’t that bothered about the files I’d lost and I’d be confident a spy, thief or Government agent would be less excited still.
Second was that I had in this case got the security trade-off wrong. Security is normally a balance between ease of use and protecting your data and I’d managed to stomp all over my ease of use for the sake of some data that neither I nor anyone else really cared about.
I’d also forgotten the obvious point that, if someone really wanted to get at my data, all they need to do was either a) get hold of the computer whilst it was running and the drive already mounted or b) get hold of me and threaten to break my legs unless I told them the passphrase (I promise you I would have cracked very quickly).
When it comes to your security, that is important. There are countless tools out there, but you need to figure out how much security hassle you want in your life, what are the threats you’re aiming to protect yourself against and what it is you’ve got that’s worth protecting from prying eyes. Otherwise, it’s entirely possible that the person who’s password is “123456” could find themselves in a much better place than the person with double-encryption and a laptop that self-destructs after five incorrect passwords are entered.
With that in mind, here are a few simple ways to boost your desktop Linux security
1. Pick a password you don’t have to write down
Traditionally we’re told about the importance of picking a long, complex password – and there’s something to that. Specifically, it makes it a lot harder for anyone who’s trying to break into your computer using a brute force attack or someone’s who’s somehow gotten hold of your hashed password file and is running cracking software against it.
But that’s unlikely to be what you have to worry about (honestly – criminals have much, much easier ways to steal valuable data than attacking individual PCs).
The threat you most likely face is someone trying to casually snoop on your data, or a work colleague thinking it would be a real laugh to send an inappropriate email, tweet or Facebook post from your account. The best way to protect against that is simply to have a password you keep to yourself and you don’t need to write down anywhere.
Oh – and do remember to leave the screen locked when you’re away from the computer.
2. Use a BIOS password
So you’ve picked a devilishly complex password for your Linux login, including lower and upper case, numbers and symbols. Shame then that the person who wants to access your files has physical access to your computer and can just boot off external media, bypassing your password completely.
Having encrypted partitions is one way to avoid this, but a simpler way which still puts a significant barrier in the way of an attacker is to enable a BIOS password that has to be entered on bootup.
3. Disable unused services
Check which services you’re running on your computer and disable ones you don’t need. If you’re not running a web server, you really shouldn’t have httpd. If you’re not acting as a secure shell server, sshd should be disabled. Not only will it free up resources on your computer, it’ll protect you should a security exploit emerge in one of those services (as they do on a fairly regular basis).
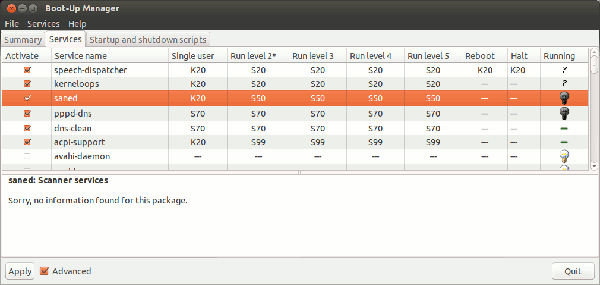
Unfortunately, although disabling services at startup is simple on Windows, it’s annoyingly complex for the non-technical user on Linux and it varies between distros. You generally need to look in /etc/init.d (having fired up a terminal and got root access) or install a graphical manager like the oh-so-amusingly-named BUM (Boot-up manager).
4. Apply patches regularly
New software patches come out all the time for Linux software – it’s normally good practice to keep your computer up to date. Make sure your distro is configured to let you know when there are patches available so you can install them.
5. Don’t trust your local network
If you’re relaxed about people being able to access your local network, that’s no problem. Quite possibly you are.
But don’t assume your network is secure. Wireless network security remains relatively trivial to crack with a host of freely available tools, and it’s much harder for a company IT department to lock down a network now everyone wants to connect not only with their work computer but with their numerous mobile devices, only some of which carry serious malware.
If you share a folder with the world on your local network, best assume the world might get hold of it.
6. Explore the privacy settings on your distro
Just as web browsers allow you to clear your history and cache, and enter private browsing mode (to access your internet bank, naturally), Linux allows you to specify how much you want your computer to remember about what you’re getting up to. Remember, though, that if someone were to break into the computer, you’ll want to use the logs to see what they got up to as well, so the privacy settings work both ways.
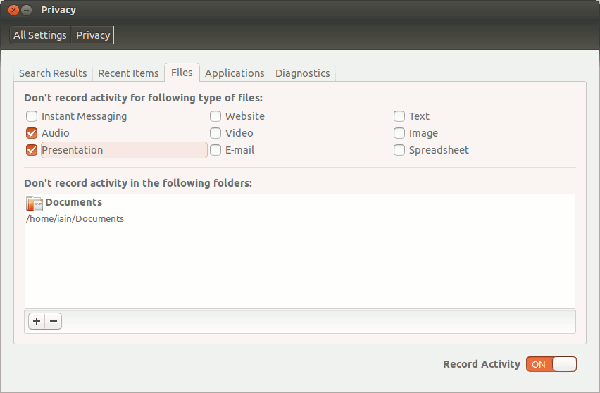
On Ubuntu 12.10, for example, you click on the top right icon on the desktop and select System Settings, then Privacy. This allows, among other things, you to stop getting Amazon purchase suggestions on the Dash, to delete your recent history and to configure Ubuntu not to record your activities on either certain applications or types of files. It will also tell you when you last used each application and how frequently you use it – if you go to the Applications tab and click +.
7. Explore encryption
Through a range of applications and services, it’s possible to encrypt pretty much everything from specific services (e.g. https, secure shell) to your entire data stream, from files and folders to emails to whole partitions. Just don’t make the same mistake I did!

{ 3 comments }
When it comes to creating passwords that are easy for me to remember yet hard for others to at least guess, I think about something that struck me as unusual on that particular day. I make a sentence out of it then pick a few consecutive letters from each resulting words so that I have at least 9-10 characters, bake some 1337 speak into it and, if the system allows it, make use of spaces.
This is a awesome post. Im sure it will be better for newbies
Physical access means that they could remove the motherboard battery, wiping out the BIOS password.