This image represents a basic network plan for a small company. The goal of this article is to use this image to help describe basic concepts of networks and how they typically constructed as well as why they are designed the way they are. Of course there are many variations to this basic design. Many times the variations depend upon the needs of the company as well as the skills of those who work for the company.
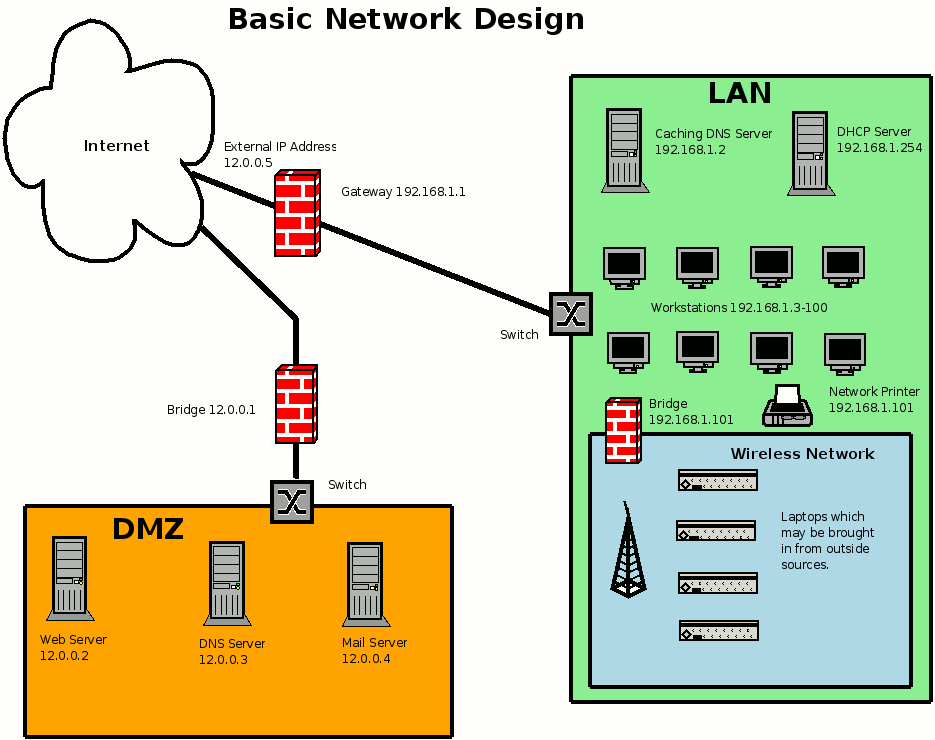
Gateway
The Gateway connects two dissimilar networks. In this example the Gateway connects the Internet to the LAN and the DMZ which are both on different networks. The Gateway, as is often the case, also performs another function in that it acts as a firewall. The firewall is doing both Nat (Network Address Translation) to the LAN and port forwarding to the DMZ. Note that the DMZ is on a different network from the LAN.
LAN
The Local Area Network (LAN) is typically where you will place your workstations. This should be the most secure area of your network as this is where your company needs to protect its data as well as the workstations on the network. Typically the LAN is on a private network, which means that these IP Addresses on the LAN are not designed to route through your Gateway nor on the Internet they are only available on the local network.
Caching DNS Server
The LAN has a Caching DNS Server which the workstations point to for DNS resolution. The caching aspect allows the LAN to have faster access to commonly accessed sites as the server will cache this information for future use. The Caching DNS Server is only available to the local network and may be used to provide DNS resolution for the local workstations.
DHCP Server
The DHCP Server provides IP Addresses automatically to the workstations, network printers and to the wireless network as people hook up laptops to it. The IP Addresses can be assigned permanently to workstations and printers so that you can map out locations easier.
DMZ
The Demilitarized Zone or DMZ is a separate network where the company will keep the pubic accessible servers like a web server, dns server and mail server. The DMZ is used to separate the public servers from the LAN because it much more likely that intrusion attempts will be made on the servers as they have services available to the public opening ports for attack. Te Gateway should be used to minimize the attacks and direct the public access only to the specific services required. For example, the Web Server should only receive traffic on port 80 and all other traffic coming from the Gateway should not be allowed. This protects the Web Server, to a degree, and cuts down network traffic.
Web Server
This is where the company web site is located. The Web Server is open on port 80 only to minimize attacks. However, in todays environment there should be a application firewall on the Web Server like Modsecurity. Most servers will be running PHP and MySQL to facilitate websites that are more interactive. This should require an application firewall to protect them properly.
DNS Server
Typically a small company will have two DNS Servers located on different subnets to provide backup for their mail and web service if one DNS server is unavailable. The DNS Server should only allow port 53 tcp and udp. It should also be configured so that the general public cannot do recursive lookups, lookups for web services that require the DNS Server to work until it finds an answer.
Mail Server
What ports are open on the Mail Server will depend upon how a company has their mail set up. Of course the MTA, Mail Transfer Agent, must have port 25 open so that all other mail can be sent and received. If your company allows web based email or POP3 will determine which other ports are open and if they are encrypted.
Bridge
The Bridge is different than the Gateway in that the Gateway typically uses NAT, Network Address Translation, to change the public IP Address 12.0.0.5), one that can route on the Internet and one that must be unique, to a private IP Address (192.168.1.1) that cannot route on the Internet and is used for internal connections. The other feature of a Bridge is that it filters traffic both with MAC Addresses, Addresses asigned to network cards, and it can filter based on iptables rules. In addition, the Bridge can be removed and it does not impact the network connectivity becaue it is not doing any NAT. This makes it a very powerful tool in protecting and monitoring your network.
In the example, the wireless network has a bridge that allows the network to accept IP Addresses from teh DHCP Server but it also protects the workstations so that a compromised laptop brought into the network would not be able to attack workstations or infect them with viruses as the traffic would be blocked by the bridge. They would however be able to access the printer or any other devices you set up in the bridge. Basically, you have the bridge to control the extra risk involved with a wireless network.
Switch
The switch is a mechanical device that separates machines so that information going to one machine is not sent to the other machines on the network. This provides reduced network usage but more importantly it provides an element of security as each machine is separated from the traffic to the other machines. Please note however, this element of security is not foolproof.

{ 6 comments }
Windows has been officially banned by Google employees. There are speculations as to why they did this, the biggest being that they’re releasing their Google OS soon. Another big one is that there are too many security difficulties with Windows. Let me break that myth down for you. Windows protection difficulties has minor to do with their quality of programming even though they do have more hackers than the others. Merely simply because they are the biggest utilized operating system in the U.S. They’re targeted! Mac would have way a lot more safety breaches if they were the biggest running method utilized. A hacker is naturally likely to target who they have probably the most access to, not the minor guys.
Depending on the data load between the DMZ and LAN and the bandwidth of the WAN connection it may be wise to add another firewalled link between the two – essentially bypassing the WAN.
Also note that switches are not “mechanical” devices, at least not any made since the invention of the transistor.
Nice I like it well done. Now a few extra thing could be mentioned for a small business setup.
1. Web server and mail server could actually be used from a hosted service thus eliminating a second internet connection. (which is a cost effective way and often done by small businesses).
2. It would be nice to mention how this set up translates in actual hardware. Just like you say the Gateway serves often as a firewall small business use a Router as a Gateway, Switch, DNS server and Firewall. Likewise the Bridge to the wireless network is often just the wireless router.
3. An apt casher is another good idea if the business is running a linux based setup.
4. Finally how will this network actually do file sharing? and allow users to use any workstation (revolving profiles). Don’t we need a some other services as well to accomplish this.
But well done and easy to understand.
Finally, a network design tutorial that isn’t Windows-centric. A Linux server can handle many times the number of clients than a Windows server can, affecting the network design accordingly.
In my Home/Small-business network, I also run caching DNS on my server. (I only need one server box thanks to the ability of a linux server to handle more load.) I have something that works but it is a real smash-up
built with hammer and tongs. I’d love to have a SOHO centric discussion of a local DNS.
Why DNS? We would like clients to use names for SOHO LAN resources without knowledge of local IP addresses. This includes not only the workstations that are always part of the “family” but other as well.
We don’t want any war chalker to access everything, but the visiting Uncle or business colleague might want to print something or share files.
Great network design post, the diagrams were great. Thanks for sharing