Distributed Monitoring
This is part two of a three part series on distributed monitoring. You can use passive service and host checks to allow non-central Nagios servers to collect data from a network of machines and then transfer that information to a central Nagios server. The transfer of information is done using NSCA so that the central Nagios server will receive the data from the External Command File interface and process the information as a passive check.
Part One: Passive Checks Course
Part Two: Central Server
Part Three: Regional Server
Nagios Training Course
Nagios Manual
In fact, in most situations you would disable service checks in nagios.cfg so that the central server can focus on it’s primary task. Edit nagios.cfg and modify these options:
execute_service_checks=0
accept_passive_service_checks=1


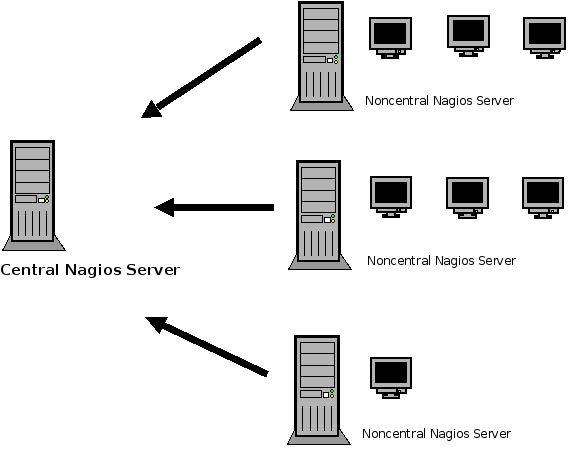
Central Nagios Server Set Up
You need to have a working Nagios server to be able to use NSCA. NSCA is not in the CentOS repository so you will need to use the rpmforge repositories. See the Nagios server install in this manual for how to install those repositories.
Install NSCA (Nagios Service Check Adaptor)
yum install nsca
Installing : libmcrypt [1/4]
Installing : xinetd [2/4]
Installing : nagios-nsca-client [3/4]
Installing : nagios-nsca [4/4]
Installed: nagios-nsca.i386 0:2.7.2-2.el5.rf
Dependency Installed: libmcrypt.i386 0:2.5.8-4.el5.centos nagios-nsca-client.i386 0:2.7.2-2.el5.rf xinetd.i386 2:2.3.14-10.el5
Set Up Interface for External Commands
The interface on the server that accepts external commands is the External Command Files which is a named pipe in /var/nagios/rw. When you install NSCA it will create this pipe once it is started.
ls -lF /var/nagios/rw
total 0
prw-rw—- 1 nagios apache 0 Sep 8 15:31 nagios.cmd|
When you send commands to the interface it will have to have the form like so:
[epoch timestamp] command;arguments
An example of the external commands can be found at http://nagios.org/developerinfo/externalcommands which lists the commands and shows examples. At this point if you are just learning the external command interface work through the examples of passive host and passive services so you better understand how they work.
Verify external commands are set up in /etc/nagios/nagios.cfg. These are the lines you need to check, typically they should be ready to go. These lines make it possible to send external commands to the Nagios server.
check_external_commands=1
command_check_interval=-1
command_file=/var/nagios/rw/nagios.cmd
log_passive_checks=1
accept_passive_service_checks=1
accept_passive_host_checks=1
Note the command_check_interval is set up so that it will accept passive communication on any time frame, it is not scheduled.
Edit /etc/nagios/nsca.cfg
Most of these settings will be there by default but you need to verify they exist.
server_port=5667
command_file=/var/nagios/rw/nagios.cmd
alternate_dump_file=/var/nagios/rw/nsca.dump
aggregate_writes=0
append_to_file=0
max_packet_age=30
These two file changes are important security issues so that the file is only accessible from the nagios user.
chown nagios:nagios nsca.cfg
chmod 400 nsca.cfg
Failure to make these security changes on a Nagios server with Internet access is asking for trouble.
Install xinetd and edit ncsa
xinetd is the superdaemon which will listen in behalf of NCSA to protect it from abuse. You will find the configuration file in /etc/xinetd.d, here is the file.
# description: NSCA (Nagios Service Check Acceptor)
service nsca
{
flags = REUSE
type = UNLISTED
port = 5667
socket_type = stream
wait = no
user = nagios
group = nagios
server = /usr/sbin/nsca
server_args = -c /etc/nagios/nsca.cfg –inetd
log_on_failure += USERID
disable = no
only_from = 127.0.0.1 192.168.5.91 192.168.4.23 192.168.3.2
}
Two important changes have been made to this file. The disable=yes have been changed to disable=no and the only_from now includes the IP Address of the clients which will connect to the server using the NSCA. Be sure to include the local host as well and separate IP Addresses with spaces.
Edit /etc/services
Be sure that Nagios can interpret the ports that are being used. If you are using NRPE list that port as well as NSCA. Edit the file with the two necessary sections the daemon and then the port followed by the protocol.
nrpe 5666/tcp # NRPE
nsca 5667/tcp # NSCA
Restart xinetd
In order to get everything working on the Nagios server you will need to restart xinetd.
service xinetd restart
Verify it is Working
By using this command you can verify that your daemon is listening on the correct port 5667 for nsca.
netstat -aunt
tcp 0 0 0.0.0.0:5667 0.0.0.0:* LISTEN
Set Up Host and Service
You will need to edit the /etc/nagios/objects/hosts.cfg so that it will accept passive connections from the client. In this example, active checks are disabled and passive checks are enabled. Be careful with the host_name as this will be used both in the configuration on the Nagios server and on the client configuration, they need to match.
The central server needs to have service definitions for all services.
define host
{
use generic-host
host_name nagios
address 192.168.5.50
active_checks_enabled 0
passive_checks_enabled 1
}
You will also need to set up a service which will provide passive checks. This will be discussed in the client section under the passive service test.
This completes the server configuration.

{ 1 trackback }