Secure FTP with SSL
FTP communication is not secure, all communication is plain text and can be easily captured. Despite this serious weakness, few do anything to secure it. There are simple ways to correct this with VSFTPD.
SSL/TLS With FTP
Add these settings to your /etc/vsftpd.conf file and you will have an anonymous ftp server that will allow anyone to download files from /home/ftp but they cannot upload. It will also protect all of your users as they must ftp into their home accounts using ssl.
anonymous_enable=YES
local_enable=YES
rsa_cert_file=/etc/ssl/certs/ssl-cert-snakeoil.pem
rsa_private_key_file=/etc/ssl/private/ssl-cert-snakeoil.key
ssl_enable=YES
force_local_logins_ssl=YES
force_local_data_ssl=YES
You do not need to create the self-signed certificate as they are already created by the vsftpd server as you can see listed. Notice that ssl is enabled only for local logins, users who have accounts on the machine. The connection will still be on port 21. Once you have the server set up you will need a client that is ftps compatible.
Here is the certificate that you will get when you connect with secure FTP.
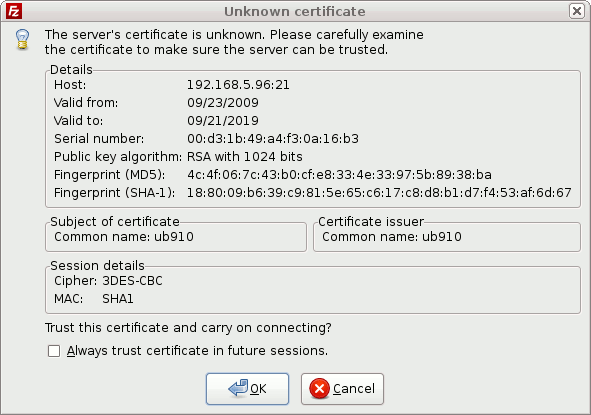
Create Self-Signed Certificate
You can create a self-signed certificate with this command which will create a certificate for 1 year and the pem file is then saved in the /etc/directory. Note that you will need to change the /etc/vsftpd.conf file to enter the path of this file. You will be asked several questions which will identify your organization.
# openssl req -x509 -nodes -days 365 -newkey rsa:1024 -keyout /etc/vsftpd.pem -out /etc/vsftpd.pem
Generating a 1024 bit RSA private key
……++++++
..++++++
writing new private key to ‘/etc/vsftpd.pem’
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
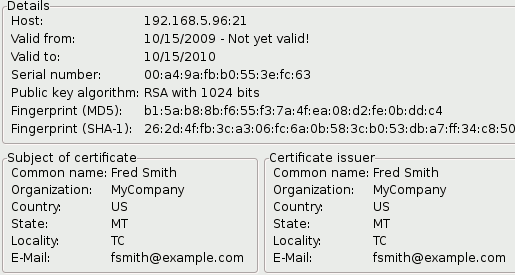
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:MT
Locality Name (eg, city) []:TC
Organization Name (eg, company) [Internet Widgits Pty Ltd]:MyCompany
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:Fred Smith
Email Address []: fsmith@example.com
This will then be reflected in the certificate when you see it.
Edit /etc/vsftpd.conf and comment out the rsa certificate and private key files that are there by default and add these lines which show the path to your self-signed certificate.
rsa_cert_file=/etc/ssl/certs/vsftpd.pem
rsa_private_key_file=/etc/ssl/certs/vsftpd.pem
Restart the ftp server.
sudo /etc/init.d/vsftpd restart
Using a FTP Client that is SSL/TLS Compatible
The popular Linux ftp client gFTP will not connect using SSL when you are using self-signed certificates, you would have to purchase a real certificate for your business. Another Linux alternative is to use ftp-ssl. This is a command line version of ftp and actually will replace ftp with this client. It functions that same as ftp. It will attempt to connect using ssl, if it is not enabled it will drop back to regular ftp. The Filezilla version for Linux is a possible alternative.
When you connect you will be asked to accept the self-signed certificate, either which you made or the default for vsftp.
Accept the certificate and you have encrypted FTP on port 21.
If you have users connecting with FileZilla you will need to make these changes so they can log in with SSL. Note the port is still 21 but the Server type is now FTP over SSL.
Now that you have the certificates installed, you can set up VSFTPD to allow local users to log on. That means that if someone has a user account on the server, you can allow him or her to log on under their own account names. You can also set up a chroot jail so that they can’t change to any directory other than their own. With the new certificates installed, you’ll be able to get around one of the big problems with traditional ftp. That is, you won’t have to worry about logon information going across the network in clear text. This is handy when you only want certain, authorized people to log on to your ftp server, instead of the whole general public. You can accomplish this with a vsftpd.conf file that looks something like this:
anonymous_enable=NO
local_enable=YES
write_enable=NO
anon_upload_enable=NO
anon_mkdir_write_enable=NO
anon_other_write_enable=NO
chroot_local_user=YES
listen=YES
ssl_enable=YES
force_local_logins_ssl=YES
force_local_data_ssl=YES
rsa_cert_file=/etc/ssl/certs/vsftpd.pem
rsa_private_key_file=/etc/ssl/certs/vsftpd.pem
You can confirm the connection using SSL to the user’s home directory by using the command:
netstat -aunt
tcp 0 0 192.168.5.33:21 192.168.5.14:2088 ESTABLISHED
Here you can see that a connection has been made, even though port 21 is used by Filezilla it is an encrypted connection. Note the secure lock at the bottom of the file to indicate that the connection is encrypted.

{ 3 comments }
I cant get it working with SSL
If I use the snakeoil certs I can login but after “227 Entering Passive Mode” I get stuck until time out.
If I make my own certificate following your howto, I cant even login…
The only way that I can login (and transfer files without problems) is deactivating completely the SSL.
Can you help me please?
Check your firewall settings. When you move to passive, the client will try to connect to the server on port 20 or whatever port you assign.
Isn’t FTP over SSL the same as SFTP or is it different to FTP over SSH?