This Nagios NSCA mini-course will provide you with the information you need so set up a Nagios server that receives passive communication from other servers and it will demonstrate how to set up a clients to send passive checks to the Nagios central server.
Course Difficulty
The course level is for an Experienced Nagios Administrator. One of the skills that you will certainly need is the ability to write your own bash or perl scripts.
Course Outline
Nagios: Passive Checks
Install NSCA on Server
Install xinetd on Server
Client Install of NSCA
Passive Host Checks
Passive Service Checks
Passive User Checks
Custom Passive Scripts
Quiz
The course provides a quiz to test your knowledge. Here is the quiz.
Course Support
The course author, among others, will be available for questions in the Forum.
There are basically two ways that Nagios can function, Active checks where Nagios is configured to actively request information from a host on regular intervals. Passive checks in which the client performs the check itself and provides the information to the Nagios server. Typically passive checks are used when a firewall prevents the Nagios server to make a request to the client or when the client is running an application that asynchronous, in other words the time schedule for a service is erratic and cannot be fully determined. Security events is one example of a situation where you do not know when the event may occur. Passive checks may also be used for distributed monitoring where you have multiple Nagios servers providing information to a master Nagios server.
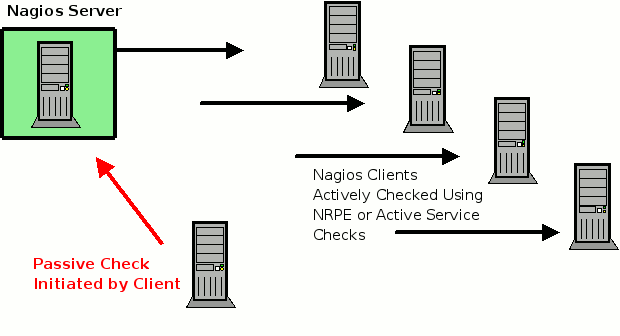
When Passive Checks are used the client uses a program called NSCA (Nagios Service Check Adaptor)and the evaluation occurs locally on the client and then is sent to the Nagios server using NSCA. NSCA runs on the Nagios server as a daemon protected by the superdaemon xinetd. The daemon will listen for requests on port 5667 sent by the client. When the server received the connects the request is authenticated using a password that is shared between the Nagios server and the client. The password is encrypted on one of ten levels to protect it as it moves over the network.
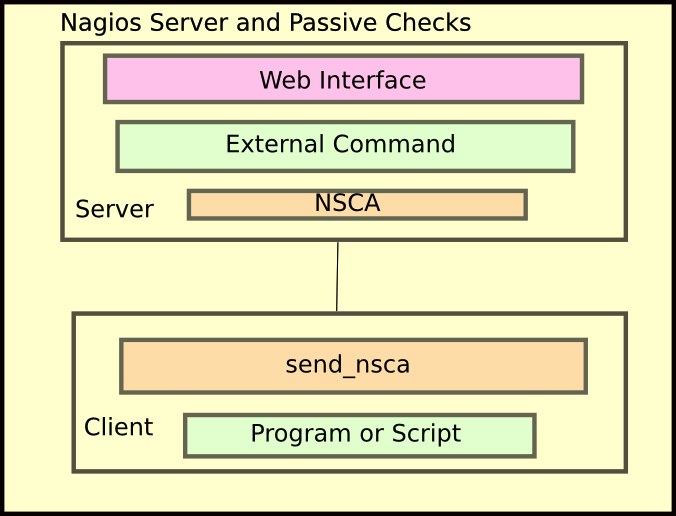
The illustration shows that on the client you must create a script that will evaluate the information you want and then send that information in the correct format to send_nsca. That is then sent encrypted over the network to the central Nagios server and received by NSCA. That is then sent to the External Commands interface when results if placing the data on the web interface.

{ 3 trackbacks }