This is a Mini-Course on the creation and use of a Stealth Firewall. This is a Free course that is available to anyone. This course will show you how to build a bridge firewall or “stealth firewall” using ebtables and iptables. This is an easy process and works on older or lightweight machines as you will see it uses Mini-ITX technology.
Stealth has an advantage of gaining access undetected. A stealth firewall provides a way to gain access to filtering Internet traffic from a position of stealth. A bridge provides stealth because it does not use an IP Address to function but rather operates at the Layer 2 of the OSI model meaning that without an IP Address the firewall is unaccessible and hidden from all would be attackers.

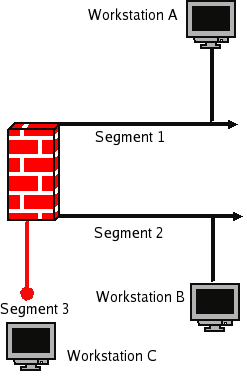
This course will show you how to build a stealth firewall that you can drop in anywhere on your network to protect some aspect of the network. Transparent or stealth bridges require little or no setup because they use the MAC address instead of an IP address to make decisions. The bridge forwards the frame from Workstation A, on segment 1, to Workstation B, on segment 2. If there was a frame for a Workstation on segment 3, it would not be forwarded to segment 2, thus reducing traffic.
Course Design
The Course is designed to take you step by step through the setup of a Bridge on a Debian Lenny Server. Much of the Free content on the Internet is disjointed and hard to follow in a logical pattern so we have decided to start building Min-Courses that focus on logical development and design to help take a student from the beginning to the end. This is a great way to start learning how to implement Linux security on an older machine.
Course Difficulty
The course level is Basic Server Administration so anyone with basic network and server skills will be able to take the course.
Course Support
The course author, among others, will be available for questions in the forum. CLICK HERE
Quizzes
The quizzes are there to help you focus on the main features of the firewall. Caution: You will only be able to take a quiz one time and that score will be recorded. So before you take the quiz be sure you understand all of the features that you will be tested on. Click Here to take a Demo Test so that you can see how the questions will be formated.
Course Outline
Advantages of a Bridge Firewall
Copyright CyberMontana Inc. and BeginLinux.com
All rights reserved. Cannot be reproduced without written permission. Box 1262 Trout Creek, MT 59874
